Microsoft is robotically enabling Home windows Prolonged Coverage on Alternate servers after putting in this month’s 2024 H1 Cumulative Replace (aka CU14).
Prolonged Coverage (EP) will robotically be toggled on by means of default when putting in Alternate Server 2019 CU14 (or later) to support Home windows Server auth capability to mitigate authentication relay and man-in-the-middle (MitM) assaults.
“This may occur when operating the GUI model of Setup and when operating the command line model of Setup with out the use of both the /DoNotEnableEP or /DoNotEnableEPFEEWS setup transfer to choose out,” stated The Alternate Group.
“In case your servers don’t seem to be in a position for the use of EP (as an example, they use SSL bridging or there are mismatches between shopper and server TLS configuration), and you don’t choose out of EP enablement right through Setup, it’s conceivable that some capability might spoil after putting in CU14.”
Admins are suggested to guage their environments and evaluation the problems discussed within the documentation of the Microsoft-provided ExchangeExtendedProtectionManagement PowerShell script sooner than toggling EP on their Alternate servers (this script robotically updates itself on techniques attached to the Web).
If encountering problems after EP is enabled, admins can both make sure that all EP necessities are met or use the script to show off the characteristic.
They are able to additionally allow EP on older variations of Alternate Server (i.e., Alternate Server 2016) the use of the similar PowerShell script on on-line servers.
Redmond additionally launched the simple-to-follow determination drift graph embedded under to lend a hand those that nonetheless wish to allow it to additional protected their Alternate atmosphere.
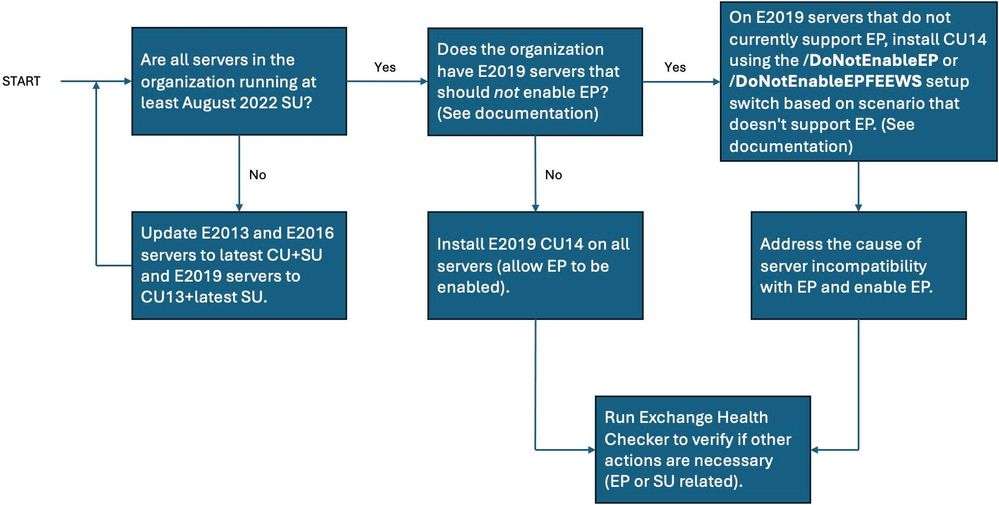
Microsoft first presented Alternate Server EP fortify in August 2022, with cumulative updates launched as a part of the August 2022 Patch Tuesday when it fastened a number of vital severity Alternate vulnerabilities (CVE-2022-21980, CVE-2022-24477, and CVE-2022-24516), taking into account privilege escalation.
Redmond stated that, but even so patching those insects, admins would additionally must allow Prolonged Coverage to make sure that attackers will not be able to breach inclined servers.
The similar request used to be made this Tuesday to totally cope with the CVE-2024-21410 vulnerability permitting faraway risk actors to escalate privileges in NTLM relay assaults.
Three hundred and sixty five days later, the corporate introduced that Alternate Prolonged Coverage can be enabled by means of default on all Alternate servers after deploying CU14.
Microsoft’s suggestions shared in August 2023 and depending on what safety replace is put in come with:
- Aug 2022 SU or later and EP enabled: Set up CU14 (no particular steps wanted).
- Aug 2022 SU or later, however EP now not but enabled: Set up CU14 with the default of ‘Allow EP’ left on.
- Alternate Server model previous than the Aug 2022 SU: “We ship you ideas and prayers, and really sturdy however mild steerage to replace your servers to the newest SU straight away.”
“We advise that each one shoppers allow EP of their atmosphere. In case your servers are operating the August 2022 SU or later SU, then they already fortify EP,” The Alternate Group stated in August 2023.
“In case you have any servers older than the August 2022 SU, then your servers are thought to be constantly inclined and will have to be up to date straight away. Additional, if in case you have any Alternate servers older than the August 2022 SU, you’ll spoil server-to-server verbal exchange with servers that experience EP enabled.”
Microsoft additionally steered shoppers twelve months in the past to all the time stay their on-premises Alternate servers up-to-date so they are in a position to deploy emergency safety patches.


