It doesn’t matter what a part of the group you’re employed in, there’s something everybody needs: a just right night time’s sleep. Everyone, from operations to safety to building, needs peace of thoughts that the entire doorways are locked, the entire networks are safe, and the group and consumers are secure. We additionally leisure more uncomplicated after we know that if anything else does move mistaken, there’s a procedure in position that may warn you simplest in the proper instances and make remediation easy.
If in case you have been tackling the realities of secrets and techniques sprawl, getting a maintain on the entire hardcoded credentials on your group, then we perceive the strain and the stressed nights that may carry. Even a small staff can upload masses of secrets and techniques a yr, so when it’s time to prioritize and get started running to get to the bottom of the recognized incidents, it may possibly appear overwhelming.
What we’d like is a technique to get some peace of thoughts that we’re nonetheless safe whilst running to remediate the issue at scale. That is the place cyber deception, within the type of honeytokens, is usually a recreation changer.
Honeytokens Can Offer protection to You Whilst You Remediate
In a really perfect international, it is advisable to remediate all of your incidents in only some mins with little handbook effort. In the true international, regardless that, this procedure can take weeks, months, or, within the worst instances, years of devoted paintings. What are you able to do to make certain that you keep secure within the interim within the tournament of a code leak or breach? Regardless of the way you construction or prioritize your reaction plan, the most efficient first step you’ll be able to take, “step 0” of remediation if you’ll, to offer protection to your self up to you’ll be able to as briefly as you’ll be able to is to deploy honeytokens to each repo with a secret leak incidence.
Deploy Honeytokens First, Ask Questions Later
Deploying honeytokens to any repos or environments the place you have got recognized a subject matter can come up with some respiring room. Understanding you have got intrusion detection and an alerting machine in position, you’ll be able to development along with your remediation plan, adjusting if one thing does move mistaken. If any person has breached your perimeter and has accessed your code, your alert will let you know to escalate, rotating the secrets and techniques they most likely discovered. In a similar way, if what you suppose is a non-public code repo all of sudden has public scanners hitting it, that means it has now transform a public repo, you’ll want to transfer that to the highest of the reaction queue.
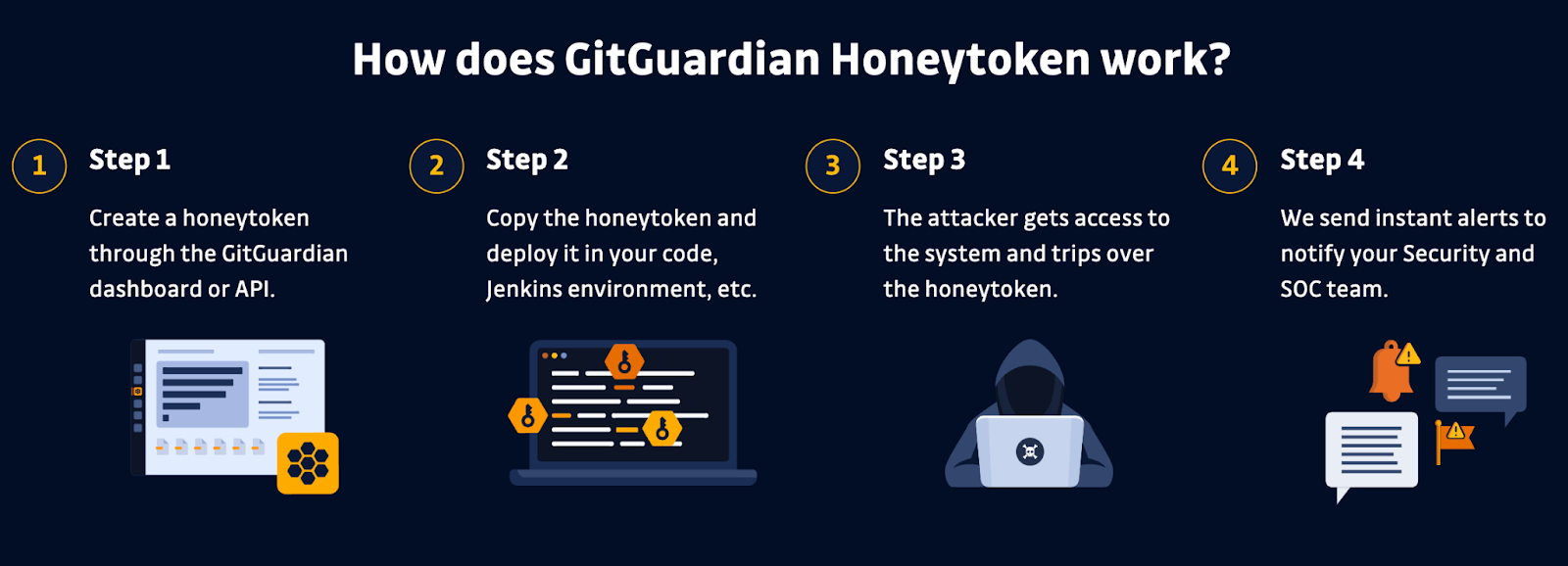
What Is a Honeytoken?
When a honeytoken is first brought on, you will have to be alerted right away by way of e-mail. The e-mail will include the entire data accrued from the tried use. You’ll be able to additionally recurrently arrange customized webhooks to ship signals to any machine you select that may parse JSON. This allows you to combine and arrange the guidelines immediately inside your SIEM or different safety programs and automate or accelerate your reaction.
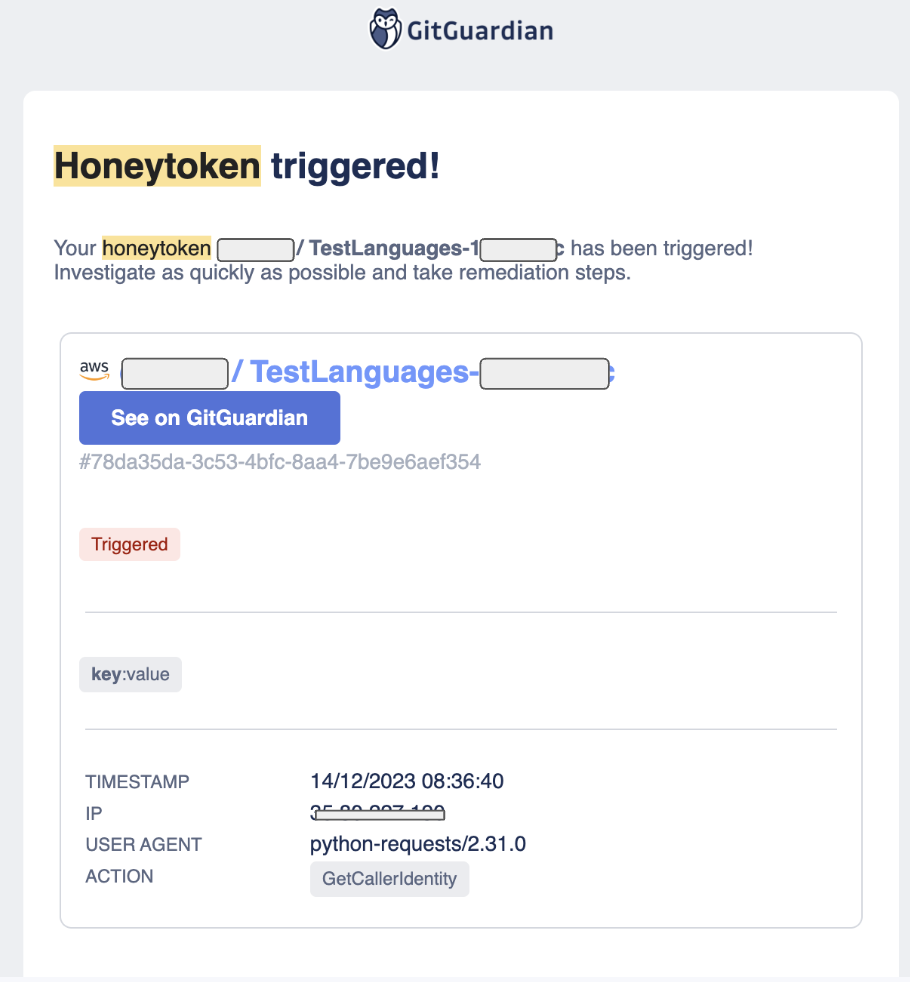
An instance alert from the GitGuardian Honeytoken machine
In maximum assaults, the opposed actors don’t manually glance via every record, line by way of line, to search out secrets and techniques. They very a lot use your secrets and techniques to transport laterally all over your machine, however as a rule, they use scanning equipment as they acquire a lay of the land. Very recurrently, those scans will right away try to use any credentials to check if they’re lively, which can cause the honeytoken. As soon as you already know they’re there, you’ll be able to react sooner than they are able to do a lot harm or exfiltrate anything else.
After getting their IP deal with and consumer agent, you’ll be able to kick them from your community and programs and briefly search for any unauthorized movements they have got taken. If there have been any legitimate secrets and techniques within the codebases the place a honeytoken used to be brought on, then it is possible for you to to escalate accurately and invalidate the ones credentials once imaginable.
For When Your Code Will get Leaked
Thankfully, we will be able to use those public scanners to our merit and leverage honeytokens to locate when non-public code turns into public. Get alerted right away when eyes out of doors your org can see your secrets and techniques. If in case you have legit, legitimate secrets and techniques in that repo, then you already know it’s time to rotate the ones secrets and techniques as briefly as you’ll be able to.
Prioritizing Your Motion Plan
Now that you’ve a technique to know if a repo is underneath assault or being shared in public, you’ll be able to prioritize your motion plan to take on secrets and techniques sprawl. You wish to have to assemble the entire wanted knowledge in a single position, carry out validity exams, and assign severity ratings.
Since there’s no legit use for honeytokens as opposed to as traps, you’ll be able to safely depart them in any wiped clean repo, giving you a similar coverage for repos with the entire actual secrets and techniques got rid of. Atmosphere it as soon as produces the long-term get advantages with none further paintings. Optimistically, regardless that, your honeytokens won’t ever be brought on.
Cleansing Up Technical Debt Takes Time
We all know that safety is difficult and reasons a large number of complications as you’re perpetually taking part in protection. We’re right here that will help you take on secrets and techniques sprawl at scale, regardless of what number of devs you have got or how a lot legacy code it’s a must to care for. Honeytokens can make certain that if any person is snooping round, they are going to cause an alert. They are able to additionally mean you can know in case your non-public code turns into public.
Honeytokens supply coverage lengthy after you get to the bottom of all of your secrets-related incidents, serving to you steadily fortify your reaction instances.