
A singular malware named ‘Agent Raccoon’ (or Agent Racoon) is being utilized in cyberattacks towards organizations in the USA, the Heart East, and Africa.
The attackers are believed to be geographical region danger actors found out through Palo Alto Community’s Unit 42, which studies seeing sufferers spanning more than a few sectors, together with executive, telecommunications, schooling, actual property, retail, and non-profit organizations.
“We assess with medium self assurance that this danger job cluster aligns to geographical region comparable danger actors because of the character of the organizations that have been compromised, the TTPs seen and the customization of the software set,” explains the Unit 42 researchers.
“We’ve got no longer showed a selected geographical region or danger crew.”
The choice of objectives, nature of the deployed gear, knowledge exfiltration strategies, focused intelligence, and the covert persona of the assaults recommend that their purpose is espionage.
Agent Raccoon backdoor
Agent Raccoon is a .NET malware disguised as a Google Replace or Microsoft OneDrive Updater that leverages the DNS (Area Title Carrier) protocol to determine a covert conversation channel with the attackers’ C2 (command and keep watch over) infrastructure.
The backdoor constructs queries with Punycode-encoded subdomains for evasion, whilst it additionally contains random values to make communications tougher to trace.
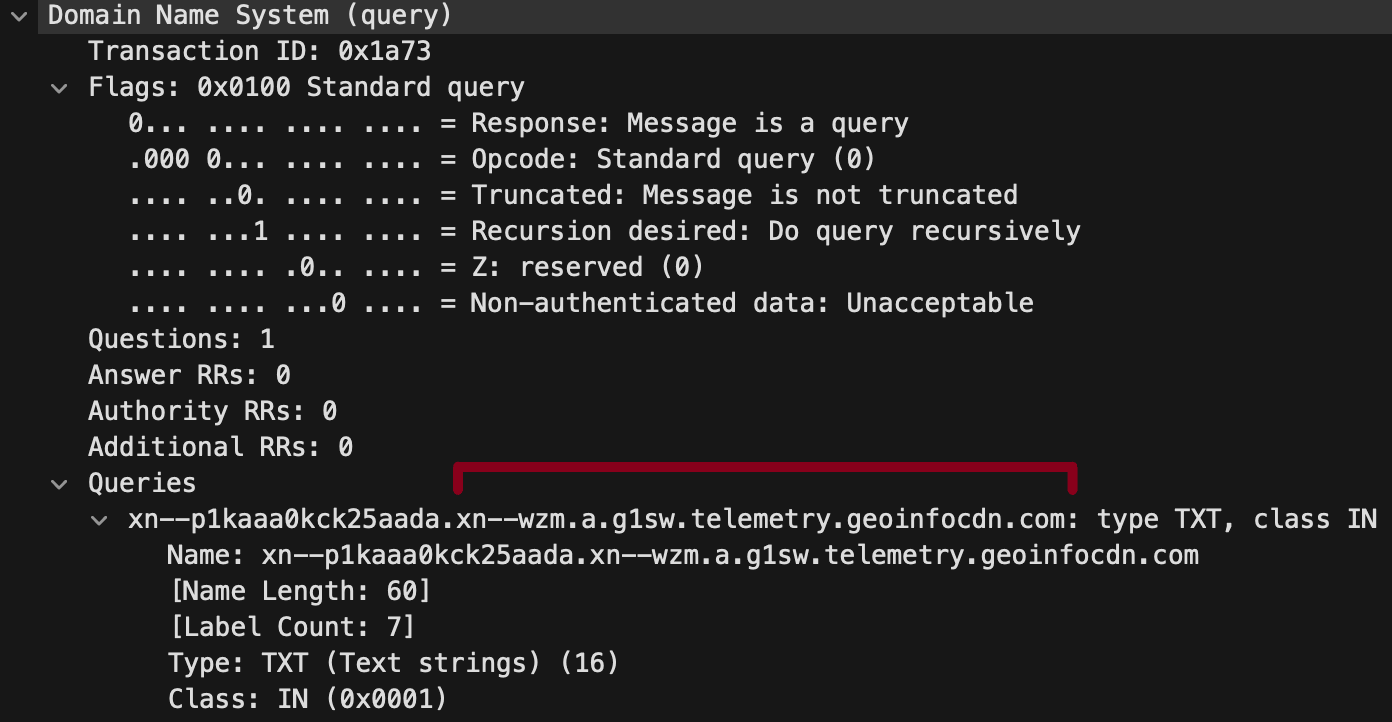
Unit 42 notes that whilst the malware itself lacks a patience mechanism, their observations recommend that it’s carried out through scheduled duties.
The malware is able to far flung command execution, document importing and downloading, and offering far flung get right of entry to to the inflamed device.
The analysts additionally be aware that they’ve captured other samples of Agent Raccoon with slight code diversifications and optimizations in its settings, indicating that the malware’s authors are actively creating and adapting it to express operational necessities.
Different distinctive gear
Except Agent Raccoon, the attackers extensively utilized a custom designed model of the Mimikatz credential dumping application, named ‘Mimilite,’ and a DLL credential stealer mimicking the Home windows Community Supplier module, named ‘Ntospy.’
Ntospy registers as a valid Community Supplier module named “credman” to hijack the authentication procedure and seize consumer credentials, a well-documented assault manner.
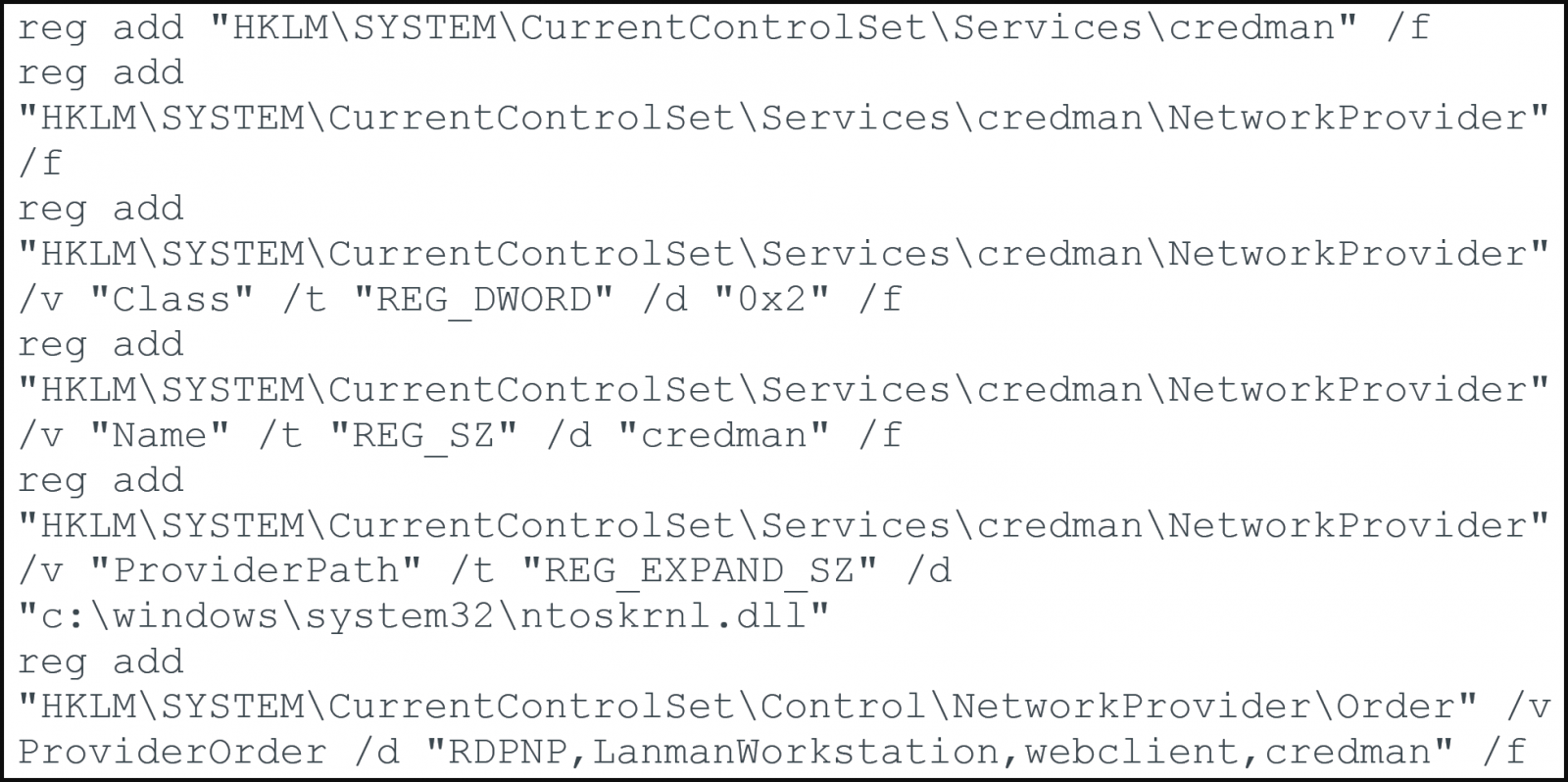
This software, too, makes use of filenames that resemble Microsoft Replace information and retail outlets intercepted credentials in plaintext shape in the neighborhood at the breached tool.
After all, the attackers use PowerShell snap-ins to scouse borrow emails from Microsoft Change servers or scouse borrow sufferers’ Roaming Profile folders, compressing the listing with 7-Zip for potency and stealth.
The seen e mail exfiltration procedure concerned distinct seek standards for every inbox, indicating a focused knowledge harvesting way that fits the presumed espionage operational profile.
The unknown job cluster has notable overlaps with every other danger actor that Unit 42 tracks as ‘CL-STA-0043,’ which is characterised as a geographical region danger actor with medium confi

