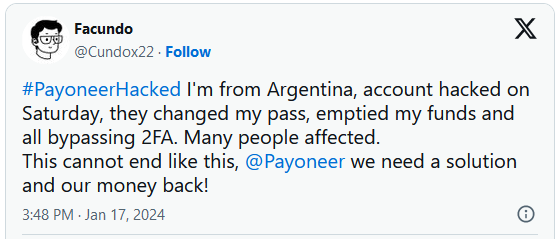
A lot of Payoneer customers in Argentina file waking as much as in finding that their 2FA-protected accounts had been hacked and budget stolen after receiving SMS OTP codes whilst they had been dozing.
Payoneer is a monetary products and services platform offering on-line cash switch and virtual cost products and services. It’s standard in Argentina as it lets in other folks to earn in foreign currency whilst bypassing native banking rules.
Beginning closing weekend, many Payoneer customers in Argentina, whose accounts had been secure by means of two-factor authentication (2FA), reported all of sudden shedding get right of entry to to their accounts or just logging in to empty wallets, shedding “years of labor” price in cash starting from $5,000 to $60,000.
The customers file that proper prior to this took place, they gained an SMS asking for approval from a password reset on Payoneer, which they did not grant. Many say they did not click on at the URLs, and a few declare now not even seeing the SMS till after the heist were finished.
Many impacted mentioned their stolen budget had been despatched to an unknown e mail cope with on the 163.com area.
Native newshounds were interviewing sufferers and monitoring the hacks and came upon that the majority affected customers had been consumers of the cell carrier suppliers Movistar and Tuenti, with the bulk the use of Movistar.
This has raised suspicions {that a} fresh Movistar knowledge leak could also be in the back of the account hacks, however the knowledge leak didn’t divulge customers’ e mail addresses, which can be required to reset passwords on Payoneer accounts.
Supply: BleepingComputer
Any other principle is that the SMS supplier used to ship OTP codes used to be breached, permitting the risk actors to get right of entry to codes despatched by means of Payoneer.
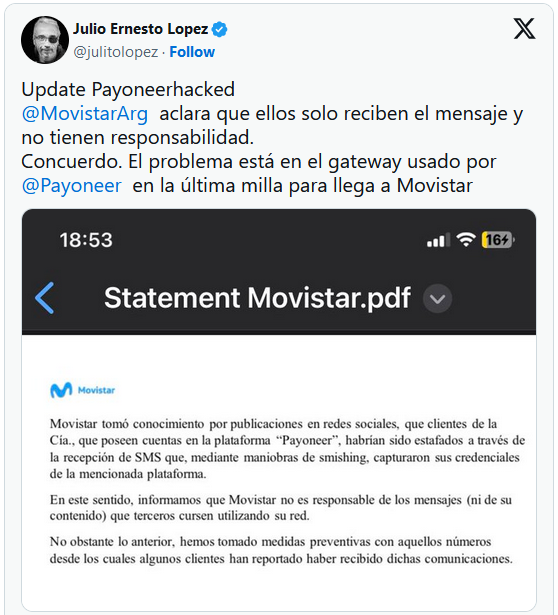
Sadly, an authentic remark from Movistar shared by means of journalist Julio Ernesto Lopez does now not cope with this principle, merely pointing out that the telecom supplier isn’t answerable for messages despatched thru its community. Then again, Movistar mentioned they’ve taken motion to dam the numbers used within the smishing marketing campaign.
“We let you know that Movistar isn’t answerable for the messages (or their content material) that 3rd events ship the use of its community,” reads the remark. (system translated)
“However the above, now we have taken preventive measures with the ones numbers from which some consumers have reported receiving such communications.”
Payoneer has now not equipped explicit solutions in regards to the assault but however said the problem and discussed it’s running with government to deal with the fraud, which it believes is the results of phishing.
Tech reporter Juan Brodersen gained a remark from Payoneer that places the blame at the customers, alleging that they clicked at the URLs within the SMS phishing texts after which entered their login main points on phishing pages.
Then again, many suffering from the account hacks state that they didn’t click on on phishing hyperlinks, accusing Payoneer of making an attempt to deflect duty and failing to recognize a possible error or vulnerability throughout the platform.
Moreover, Lopez advised BleepingComputer that Payoneer calls for a brand new SMS OTP code to be entered whilst you upload a brand new vacation spot cope with and however whilst you cord cash. If this used to be a phishing assault stealing OTP codes for the password reset, the risk actors will have to now not have had get right of entry to to later OTP codes required for those transactions.
Whilst the hacks could also be allowed by means of a 2FA bypass computer virus, like we noticed closing 12 months with Comcast, different international locations would most likely be suffering from the assaults.
Because of this, the assault’s actual mechanism stays unclear, with more than a few hypotheses at play. A vital weak spot in Payoneer’s device is its reliance on SMS-based 2FA, additional compounded by means of the platform’s password restoration procedure, which most effective calls for an SMS code.
BleepingComputer has contacted Payoneer with a request for a remark at the above, the standing in their investigation, and whether or not they plan to provide restitution within the case {that a} weak spot in its device is came upon to be the supply of the hacks, however now we have now not heard again but.
Till the placement clears up on who is responsible and what precisely took place, Payoneer customers in Argentina are prompt to withdraw budget from their accounts or disable SMS-based 2FA and reset their account password.